Man-in-the-Middle (MitM) Attack
Man-in-the-Middle (MitM) Attack
A Man-in-the-Middle (MitM) attack is a type of cyberattack where an attacker secretly sits between two communicating parties (for example, your laptop and a website) and relays — and often alters — the messages between them. To the victim, everything looks normal, but the attacker can read, inject, or modify data in transit. This makes MitM attacks dangerous because they can expose passwords, financial details, private messages, and other sensitive information without the user realizing anything is wrong.
In simple terms, a Man-in-the-Middle attack is when an attacker positions themselves between two systems that believe they are communicating directly with each other. The “middle” party intercepts traffic, and can:
- eavesdrop — silently read the exchanged information;
- modify — change the content of messages, e.g., alter transaction amounts;
- impersonate — pretend to be one endpoint to the other, enabling credential theft or session hijacking.
MitM can happen on many layers (network layer, application layer) and against various protocols (HTTP, HTTPS if improperly implemented, email, or even cellular communications).
Typical Attack Flow
Conceptually a MitM attack follows three phases:
- Positioning: the attacker inserts themselves on the path between client and server.
- Interception: the attacker intercepts or captures traffic flowing between the two.
- Exploitation: the attacker reads, logs, modifies, or forwards the traffic to complete the illusion of normal communication.
User Request to the Server
Normal flow: when you click a link or submit a form, your device opens a connection to the server (for example, a website). Your request is routed through routers and ISPs to the server, which processes it and sends back a response. Secure connections use cryptographic protocols (TLS/SSL) so only you and the server can read the content.
Compromised flow: during a MitM attack, the attacker makes you believe you are talking to the real server while they transparently relay (and possibly alter) messages. From your browser’s viewpoint the request appears to succeed; from the server’s viewpoint the request appears to come from your IP — but in fact both ends are talking through the attacker.
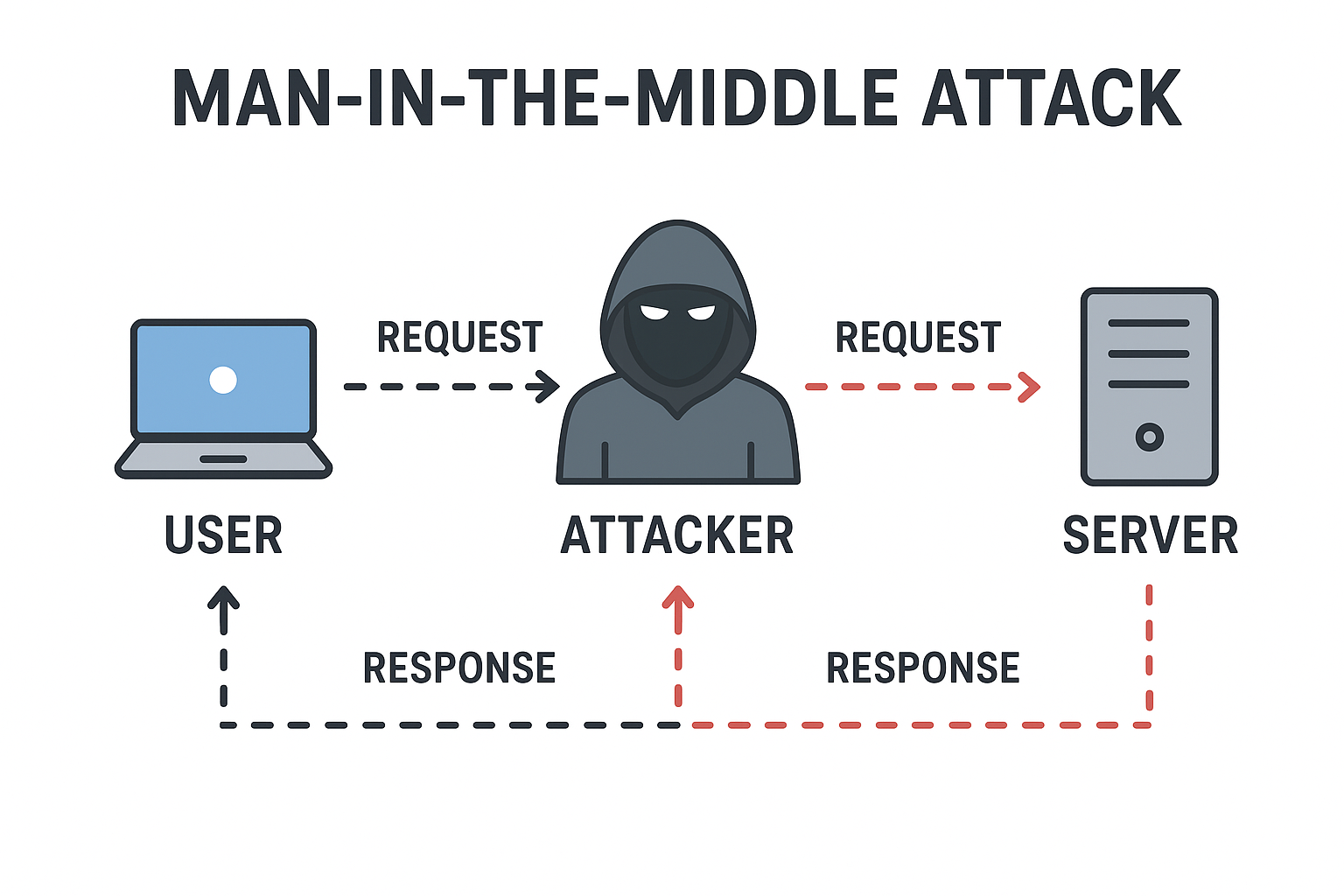
How the Attacker Intercepts the Request
Attackers use many techniques to get between you and the server. Here are common interception methods explained simply:
Rogue or Malicious Wi-Fi Access Points
An attacker sets up an access point with a familiar or enticing name (for example, “CoffeeShop_Free_WiFi”). If you connect, the attacker controls the network gateway and can capture or modify your traffic.
ARP Spoofing / ARP Poisoning (Local Network)
On a local Ethernet or Wi-Fi network, devices use ARP (Address Resolution Protocol) to map IP addresses to MAC addresses. An attacker can send fake ARP replies so that other devices associate the attacker’s MAC address with the gateway’s IP. Traffic intended for the gateway is then sent to the attacker first.
DNS Spoofing / DNS Hijacking
DNS translates human domain names (example.com) into IP addresses. If the attacker poisons DNS responses or hijacks a DNS server, they can make your browser go to the attacker’s server instead of the real one while the URL looks correct.
SSL/TLS Stripping and Downgrade Attacks
If a site supports both HTTP and HTTPS, an attacker might force or trick the client into using an insecure HTTP connection (or present a fake certificate) so they can read and alter traffic. Properly enforced HTTPS and HSTS reduce this risk.
Proxy or Transparent Proxy Deployment
In some environments (malicious or misconfigured), traffic is routed through a transparent proxy that inspects and potentially modifies content. Attackers can set up such proxies to intercept traffic at scale.
Compromised Routers, ISPs, or Network Equipment
If network infrastructure devices are compromised — whether at home, in an enterprise, or within the service provider — attackers can redirect or duplicate traffic for inspection.
Server Response: What the Attacker Does with It
After intercepting the request, the attacker receives the server’s response and can:
- Relay it unchanged so neither side detects latency or obvious tampering (passive eavesdropping).
- Modify it to inject malicious scripts, change links, alter data (active manipulation).
- Store/Log it to capture credentials, cookies, or session tokens for later use.
- Block or delay it to create confusion or cause retransmissions that reveal additional data.
If TLS is used and properly validated by the client, the attacker cannot read or alter the encrypted content without breaking the secure connection (unless they control a trusted certificate or the user accepts a forged certificate). However, attackers often rely on users ignoring certificate warnings or use techniques like deceptive certificates, stolen CA keys, or client-side misconfigurations to bypass TLS protections.
Signs of a Possible MitM Attack
What Users Might Notice
- Unexpected TLS/SSL certificate warnings in the browser.
- Frequent, unexplained logouts or authentication failures.
- Sudden appearance of unfamiliar login pages or redirects.
- Strange content injected into webpages (popups, forms, links) or altered transaction details.
- Unusually slow or inconsistent network performance when other devices are fine.
Defenses and Best Practices
Preventing MitM attacks relies on defense in depth:
- Always use HTTPS and verify certificates — do not ignore certificate warnings.
- Prefer networks you trust; avoid sensitive transactions on public Wi-Fi without a trusted VPN.
- Use a reputable VPN when on untrusted networks — it encrypts traffic from your device to the VPN server.
- Enable HSTS on websites you control and use secure cookie flags (Secure, HttpOnly, SameSite).
- Keep devices and routers updated, change default passwords, and disable unused services.
- Use multi-factor authentication so stolen credentials alone are not enough to access accounts.
- Network admins can deploy ARP and DHCP protection, DNSSEC, TLS inspection only with strict controls, and monitoring for unusual ARP/DNS activity.
A Man-in-the-Middle attack works by stealthily placing an attacker between two communicating parties so they can read, modify, or hijack traffic. It leverages network weaknesses, misconfigurations, or user mistakes. Awareness (watching for certificate warnings and odd behavior), using encryption correctly, and following practical security measures (VPNs, MFA, up-to-date devices) dramatically reduce the risk of becoming a victim.